
Secure CPS Design Strategies
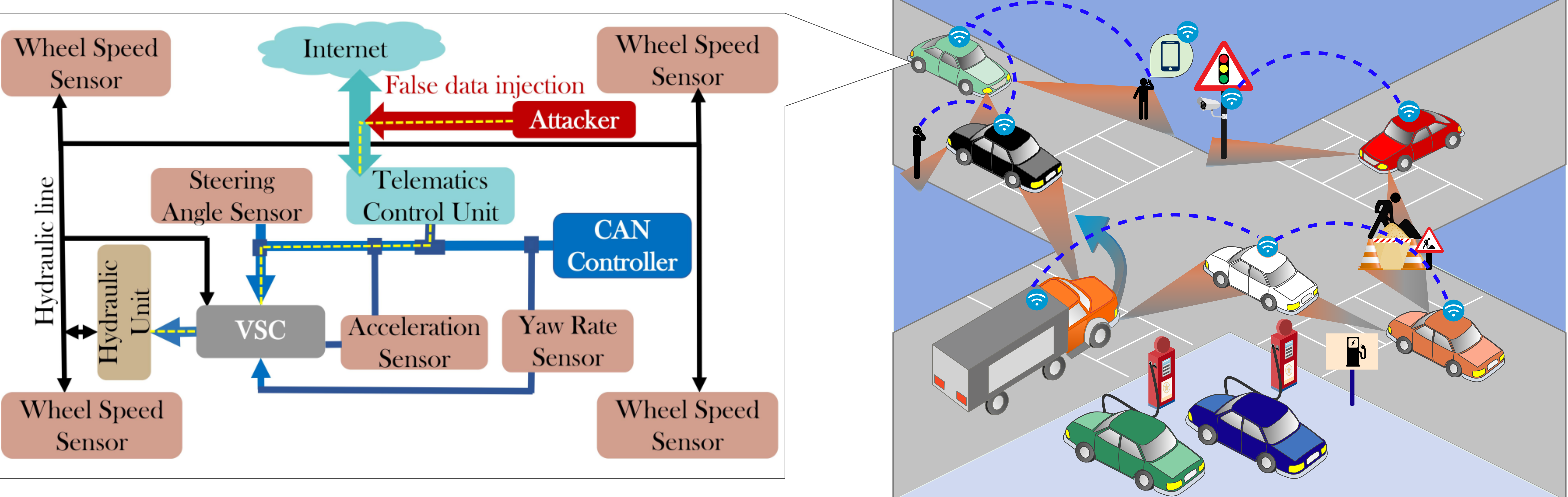
Vulnerabilities in Automated Vehicles
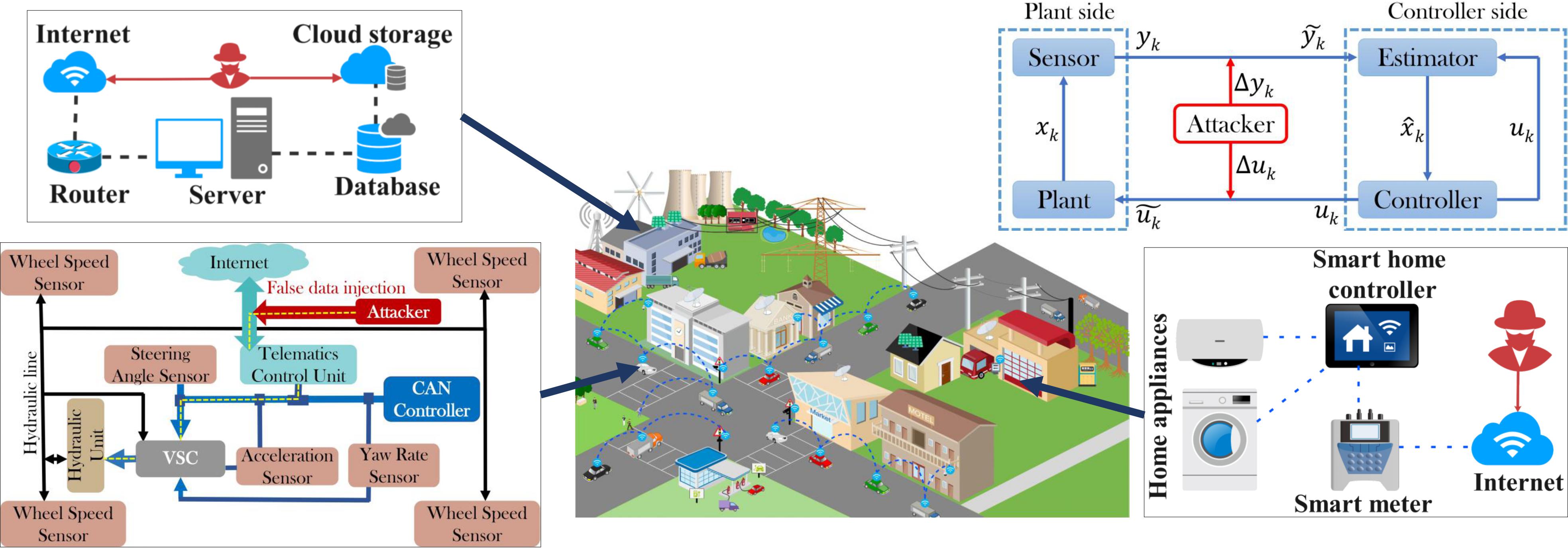
Vulnerabilities in modern day CPS
Recent Popularity of Cyber-Physical Systems (CPS) spans through several domains from automotive to power distribution systems. Advancement in CPS research has enhanced features like connectivity and automation enabling a large area coverage with least human effort in such systems. As an example, Automated Connected Vehicles, Smart grid and Smart Building management Systems, IoT devices are becoming more common place. But these boons of sophistication come with an inevitable let down of more exposure towards malicious intents jeopardising the safety requirements of such systems.
Attackers are not bounded to remotely unlocking the car doors anymore. They are becoming smarter by demonstrating not only physical but also remote carjacking. Few years back Charlie Miller and Cris Valasek has proved how vulnerable the automobiles are becoming. They demonstrated Zero-day like cyber attacks on vehicles from manufacturers like JEEP (Cherokee),Fiat (Chrysler). Such vulnerabilities obligated new legislations for automobile vendors to meet certain protection standards for sold vehicles. Even after that there have been several incidents of Wireless Carjacking. Targeting large scale CPS vulnerabilities is not new. We have seen how a 500kb computer code (Stuxnet) can destroy Atomic Power Establishments in 2010 by compromising programmable Logic Controllers, which is hugely used in any embedded systems! By remotely shutting down power supply of Ivanofranivsk region of West Ukraine in 2015 the attackers proved their strategies are also improving as new-age CPS offers them a huge attack surface. So our research is primarily aimed to eliminate such ill-intents to challenge CPS safety without compromising their usual functionalities.
Most of the CPS we intent to provide security are Safety-Critical. So we explored formal methods to find security loopholes by analysing safety of such systems as they continue to function in real world. This analysis helps understand how robust the control systems are towards such anomalies. More on this is described in Safety-Critical CPS Verification topic.

Mitigating security vulnerabilities in CPSs are not only addressing usual software security or all about utilizing cryptographic practices but needs an in-depth knowledge about system functionalities. The reason is these vulnerabilities are not generic. For addressing such vulnerabilities, we can improve control behaviour of the system to be robust against such attacks. The protection system design can be integrated well by exploiting the control structure of the system. We also research on lightweight security components popular among cryptography researchers like Physically Unclonable Functions (PUFs) because of their resource constraints. This is another aspect of CPS like automobiles or IoT devices we need to contemplate while designing security mechanisms since most such systems are limited on resource. So, we try to ensure the security along with ensuring desired performance profile of the CPS.
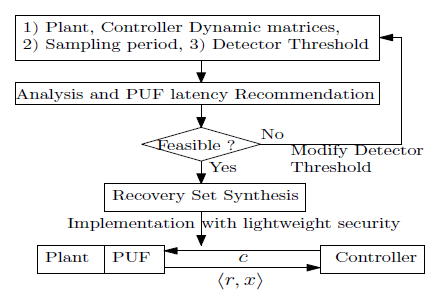
Developing lightweight security measures with performance guarantee is not enough when we are talking about resource constrained CPSs. Because prioritized safety-critical tasks must not be harmed while spacing the security tasks in place. For this Control-Scheduling Co-design approach comes in our research space. For more details on such works visit Automotives Section of our research domains.