Privacy Preserving Smart Grid Information Flow
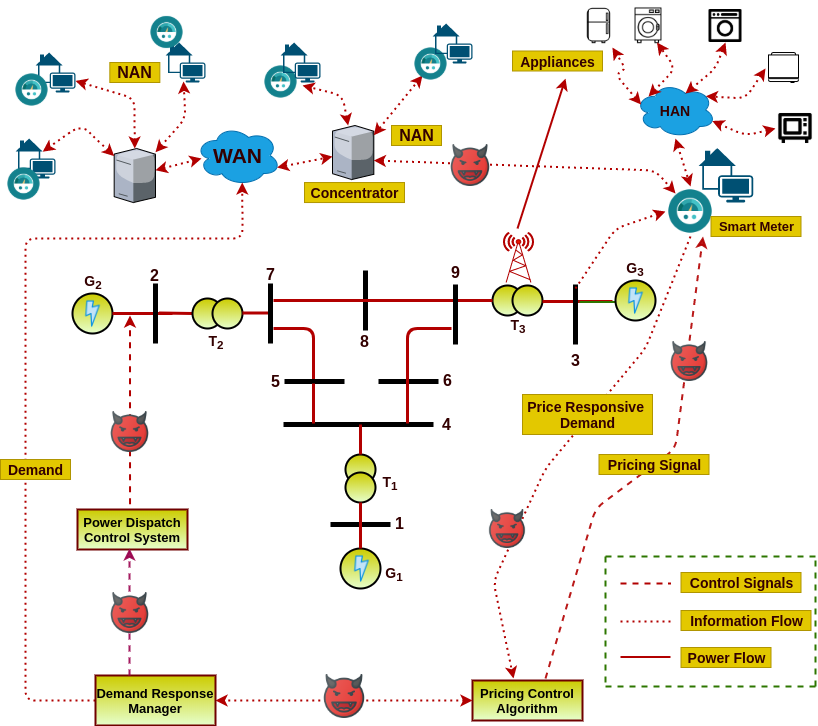
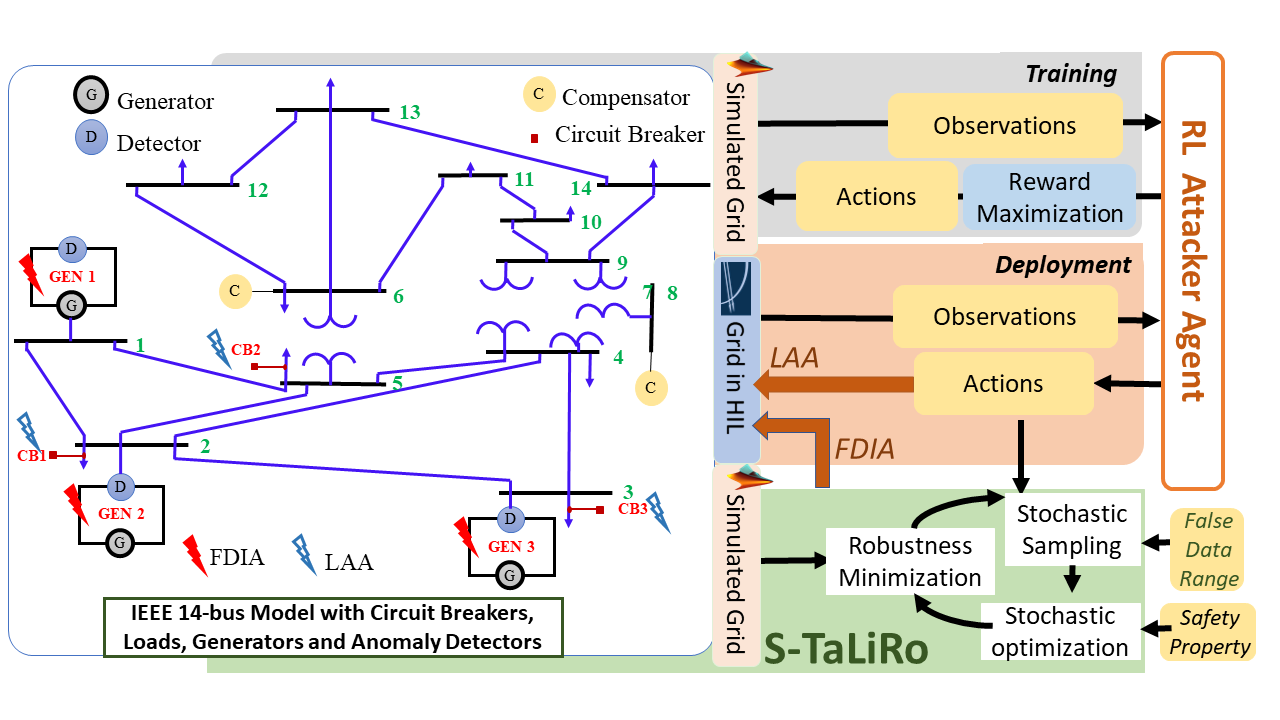
A Smart Grid is a large scale Cyber Physical System comprising generation, distribution systems, metered loads, system state sensors and support for multiple real time communication protocols. Given the exponential growth of electricity consumption, modern grid systems implement sophisticated energy management and load balancing systems. Smart meter fulfills these expectations and provides a greater value for both supplier and customer sides. Smart meters and customers are some of the essential components of a smart grid to maintain a bi-directional flow of electricity and informative data for different operational purposes such as managing energy usage, timely billing, failure detection, demand response, load monitoring etc. The figure shows a Smart Grid architecture example employing an IEEE 9-bus power system model along with pricing as well as metering loops. The design and implementation principles of this kind of Cyber Physical System (CPS) are significantly different from other embedded systems because of the tight coupling of real valued and dense time system dynamics with software based discrete automated control.
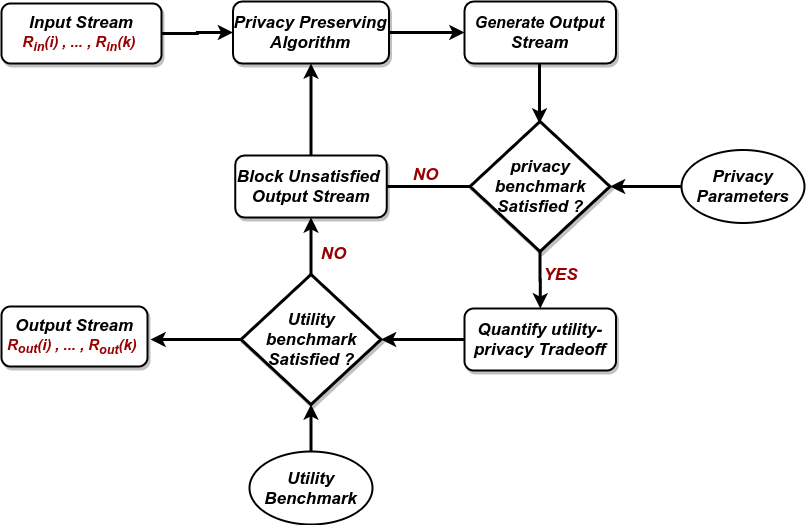
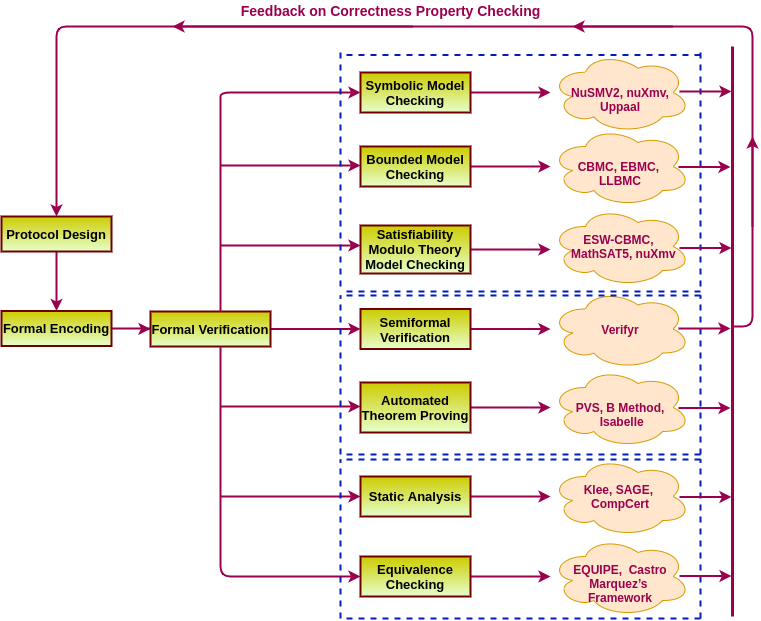
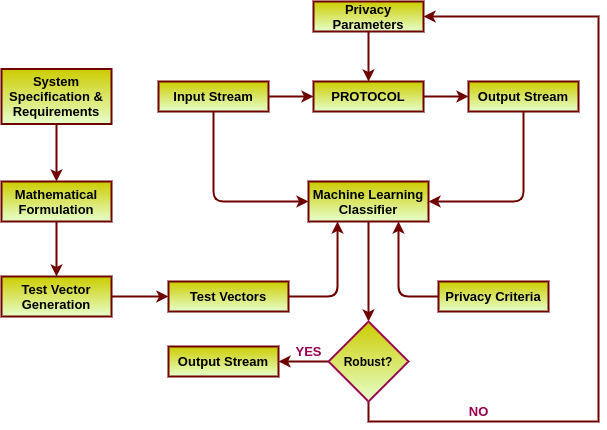
In available literature, people usually concentrate on separate control planes of the grid; either the power network or the communication network or a combination of both for satisfying different control objectives like economic dispatch, privacy aware metering, pricing control and demand response. However, for considering the security perspective, the interaction of these loops need to be modeled, an aspect we bring in for the our current work. In the figure, the dotted red lines display the vulnerable attack channels of this architecture. Minor tempering of control signals in such systems can lead to blackout of grid infrastructure. Also, on the other hand, various studies have shown that the closed loop formed by the real-time pricing signals and (semi-)automated/manual demand response by consumers, appliances and lower level distribution frameworks can be exploited by an adversary to destabilize the control objective of pricing schemes. Small malicious modifications to the price signals or the demand can be continuously amplified in the closed loop to trigger grid inefficiency and cascaded failures leading to blackouts. Smart Grid communication infrastructure supports very low bandwidth, thus high-end cryptographic security solutions are unsuitable for such systems. This motivates approaches for lightweight privacy-preserving smart meter data streaming. Moreover, the effect of such techniques on real time electricity pricing is also something worth exploring since pricing signals operate in closed loop with user consumption patterns and adversarial attacks on such signals can potentially destabilise real time pricing algorithms causing huge financial loss to the utility provider. Our present work outlines a road map for verifiable privacy preserving data streaming protocol design given a formalized definition of privacy and usability of smart meter data. The robustness of such protocols is further tested in our work with Machine Learning based attacks which attempt to reverse engineer the data streams. Also we further study the effect of privacy transformations in the context of pricing loop sensitivity.Read More